Stuff for the Stash, Week 48
My personal take on what I found noteworthy in the field of cybersecurity this week
Welcome to this weekly roundup of internet things which I added to my collection of interesting things.
The beings that dwell the depths of the internet have been fairly active, so settle in for some interesting reading.
The week’s keywords include #sgx, #clang, #carhacking, #awsnitro, #apple, #esim, #scada, #riscv, #decnet, #historicalcomputing, #freebsd, #bluetooth, #vulnerabilities, #ics, #ot and #nis2.
Comments, suggestions and story submissions are always welcome !
Blogs and other news
An overview of publicly known Intel Software Guard Extension (SGX) attacks got its own website at https://sgx.fail/ .
A short but interesting article about a topic many people commonly forget. Undefined behaviour is not the same as implementation-defined behaviour, and trying to handle undefined behaviour might result in the compiler optimizing your checks away, in this case for an integer overflow. Jump off the deep end with GCC undefined behaviors are getting wild, the related GCC bug and discussion, A guide to Undefined Behavior in C and C++, Falsehoods programmers believe about undefined behavior.
Game controllers, USB, hacking, dumping firmware, all in one article ? Yep, you can read it at Hacking microcontroller firmware through a USB
Good security improvements in vehicles, such as encryption, OTA software updates and “intrustion detection” possibly also lead to vehicles becoming less accessible to hobbyists or people who want to work on their own vehicles. In this article specific to the upcoming 2024 Ford Mustang, tuners are not happy. This makes me think of the discussion surrounding the DRM John Deere has on their farm machinery and I suspect a healthy hacking scene will continue to exist for the time being for vehicles as well. https://www.themanual.com/auto/2024-ford-mustang-will-be-hard-to-tune/
You can game the core type allocation system of Apple silicon by running tasks in a virtual machine. Full article is at Can you game core allocation on Apple silicon?
The Amazon AWS Nitro system is the platform on which EC2 instances live. The Nitro system is decoupling CPU, storage, networking, management capabilities etc and offloads them to dedicated hardware and software. As usual these days, this design choice carries claims of improved security.
Three key components of the Nitro System achieve these goals:
Purpose-built Nitro Cards — Hardware devices designed by AWS that provide overall system control and input/output (I/O) virtualization independent of the main system board with its CPUs and memory.
The Nitro Security Chip — Enables a secure boot process for the overall system based on a hardware root of trust, the ability to offer bare metal instances, as well as defense in depth that offers protection to the server from unauthorized modification of system firmware.
The Nitro Hypervisor — A deliberately minimized and firmware-like hypervisor designed to provide strong resource isolation, and performance that is nearly indistinguishable from a bare metal server.
Amazon goes a little more in depth on the security design of the AWS Nitro sytem at https://docs.aws.amazon.com/whitepapers/latest/security-design-of-aws-nitro-system/security-design-of-aws-nitro-system.html .
Papers
All of us have heard about eSIM, the technology which is replacing removable SIM cards. This paper picks apart the “Remote SIM provisioning protocol”. Paper at “Security Analysis of the Consumer Remote SIM Provisioning Protocol”
The analysis shows that the consumer RSP protocol protects against a network adversary when all the intended participants are honest. However, we also model the protocol in realistic partial compromise scenarios where the adversary controls a legitimate participant or communication channel. The security failures in the partial compromise scenarios reveal weaknesses in the protocol design. The most important observation is that the security of RSP depends unnecessarily on it being encapsulated in a TLS tunnel. Also, the lack of pre-established identifiers means that a compromised download server anywhere in the world or a compromised secure element can be used for attacks against RSP between honest participants. Additionally, the lack of reliable methods for verifying user intent can lead to serious security failures. Based on the findings, we recommend practical improvements to RSP implementations, to future versions of the specification, and to mobile operator processes to increase the robustness of eSIM security.
From the world of “EDR for SCADA” comes this paper on detecting ICS attacks by correlating behaviours against a limited set of legitimate behaviors. Full paper is titled “SCAPHY: Detecting Modern ICS Attacks by Correlating Behaviors in SCADA and PHYsical”
Using this established behavior, SCAPHY selectively monitors attackers physical world-targeted activities that violates legitimate processcontrol behaviors. We evaluated SCAPHY at a U.S. national lab ICS testbed environment. Using diverse ICS deployment scenarios and attacks across 4 ICS industries, SCAPHY achieved 95% accuracy & 3.5% false positives (FP), compared to 47.5% accuracy and 25% FP of existing work. We analyze SCAPHYs resilience to futuristic attacks where attacker knows our approach.
A paper was released titled “Control-Flow Integrity at RISC: Attacking RISC-V by Jump-Oriented Programming”. Maybe elementary, but surely interesting to some.
This paper demonstrates that RISC-V is sensible to Jump-Oriented Programming, a class of complex code-reuse attacks, able to bypass existing protections. We provide a first analysis of RISC-V systems' attack surface exploitable by such attacks, and show how they can be chained together in order to build a full-fledged attack. We use a conservative hypothesis on exploited registers and instruction patterns, in an approach we called reserved registers.
Bits and Pieces
A nice article on how a bug related to the Stack Segment register was fixed in hardware on the 8086! processor. Click for the nice and detailed 8086 die pictures. https://www.righto.com/2022/11/a-bug-fix-in-8086-microprocessor.html
Some hobbyists are still maintaining a DECnet network to this day. Interesting if you’re a fan of oldschool networking technologies. http://mim.stupi.net/hecnet
WireViz is a tool to easily document cables and wiring harnesses in clean diagrams based on text input files. https://github.com/formatc1702/WireViz
Visual6502 simulates visually how multiple historic processors operate. Very interesting visualisation. ARM1 visual SIM
Vulnerabilities
There’s a stack overflow in FreeBSD ping. https://www.freebsd.org/security/advisories/FreeBSD-SA-22:15.ping.asc
The pr_pack() copies received IP and ICMP headers into stack buffers for further processing. In so doing, it fails to take into account the possible presence of IP option headers following the IP header in either the response or the quoted packet. When IP options are present, pr_pack() overflows the destination buffer by up to 40 bytes.Google found a nice use-after-free and infoleak in the Bluetooth L2CAP protocol. Write ups at Linux Kernel: UAF in Bluetooth L2CAP Handshake and Linux Kernel: Infoleak in Bluetooth L2CAP Handling
An IoT thing has bugs (*collective gasp*), and there’s a few hundred thousands on the internet. Detailed article explaining the vulnerabilities and exposure at https://vulncheck.com/blog/xiongmai-iot-exploitation
Three new vulnerabilities in OT products by Festo and CODESYS, including a high severity one in the Festo Generic Multicast protocol. https://therecord.media/three-vulnerabilities-found-affecting-ot-products-from-german-companies-festo-and-codesys/
CISA released seven new Industrial Control System advisories. https://www.cisa.gov/uscert/ncas/current-activity/2022/11/29/cisa-releases-seven-industrial-control-systems-advisories
Want to know all the bugs NIST recorded in their database during the week of November 21 ? Here they are: https://www.cisa.gov/uscert/ncas/bulletins/sb22-332
Policy things
The US Government Accountability Office delivers a “Pants On Fire”-warning to the Department of the Interior's Bureau of Safety and Environmental Enforcement (BSEE) that the offshore Oil and Gas industry to start getting their act together.
GAO is making one recommendation: BSEE should immediately develop and implement a strategy to address offshore infrastructure risks. Such a strategy should include an assessment and mitigation of risks; and identify objectives, roles, responsibilities, resources, and performance measures, among other things.
Want to know what other organisations spend their cybersecurity budgets on ? ENISA has published their third NIS investments report digging into exactly that question. Report PDF here.
[…] which collects data on how Operators of Essential Services (OES) and Digital Service Providers (DSP) identified in the European Union’s directive on security of network and information systems (NIS Directive) invest their cybersecurity budgets and how this investment has been influenced by the NIS Directive. In addition, global cybersecurity market trends are presented through Gartner security data and insights observed globally and in the EU, in order to provide a better understanding of the relevant dynamics. This year's report presents data collected from 1080 OES/DSPs from all 27 EU Member States and can now provide a historical dataset that allows for year-on-year comparison and identification of trends.
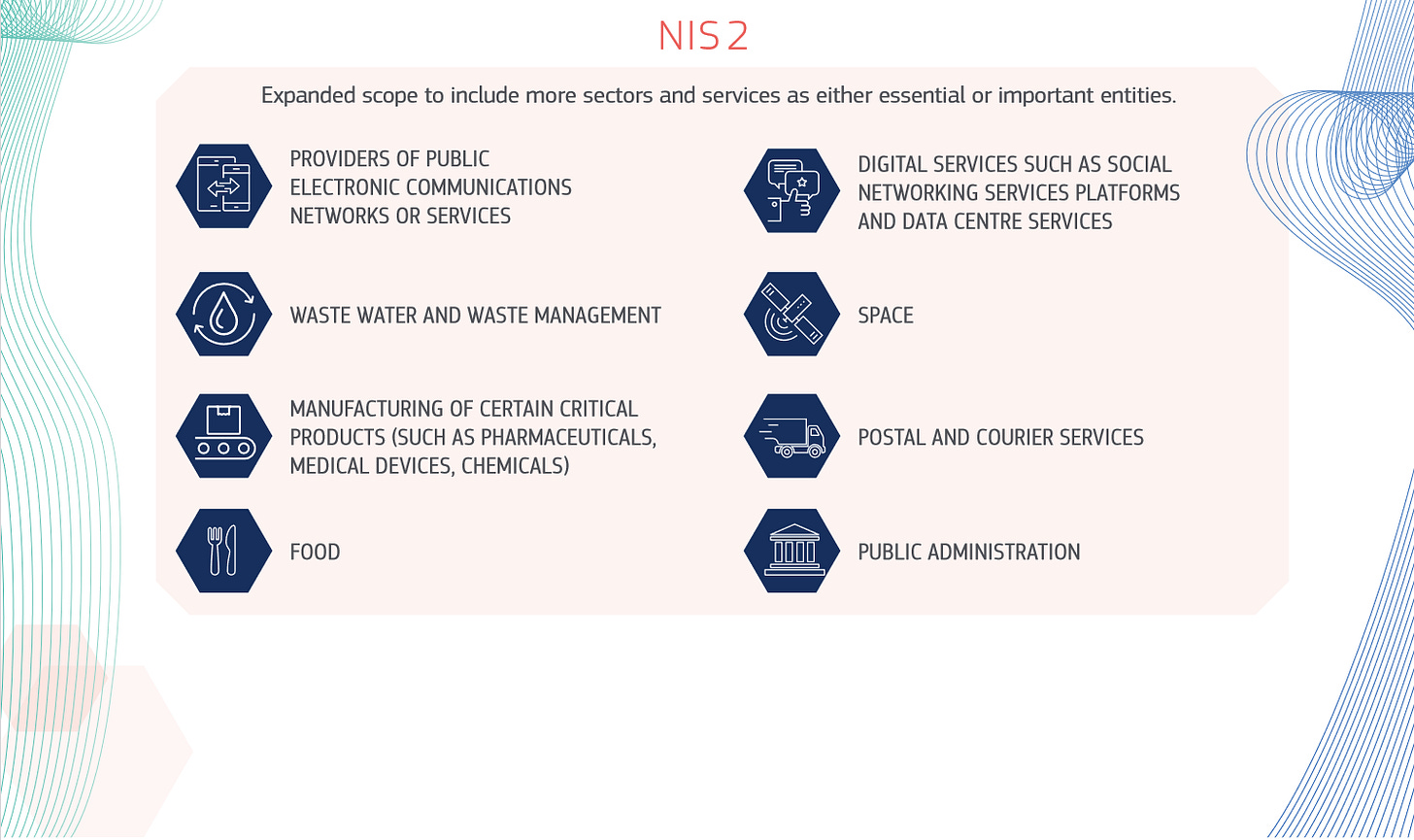
At the same time, the European council has now formally adopted NIS2, which widens the scope of these roles for industries that are subject to the directive, such as energy, transport, health and digital infrastructure. Member states now have 21 months to adopt the new rules, so I fully expect we will start hearing much more about this topic soon. Announcement
That’s it for this week. Take it easy everyone !
Thierry